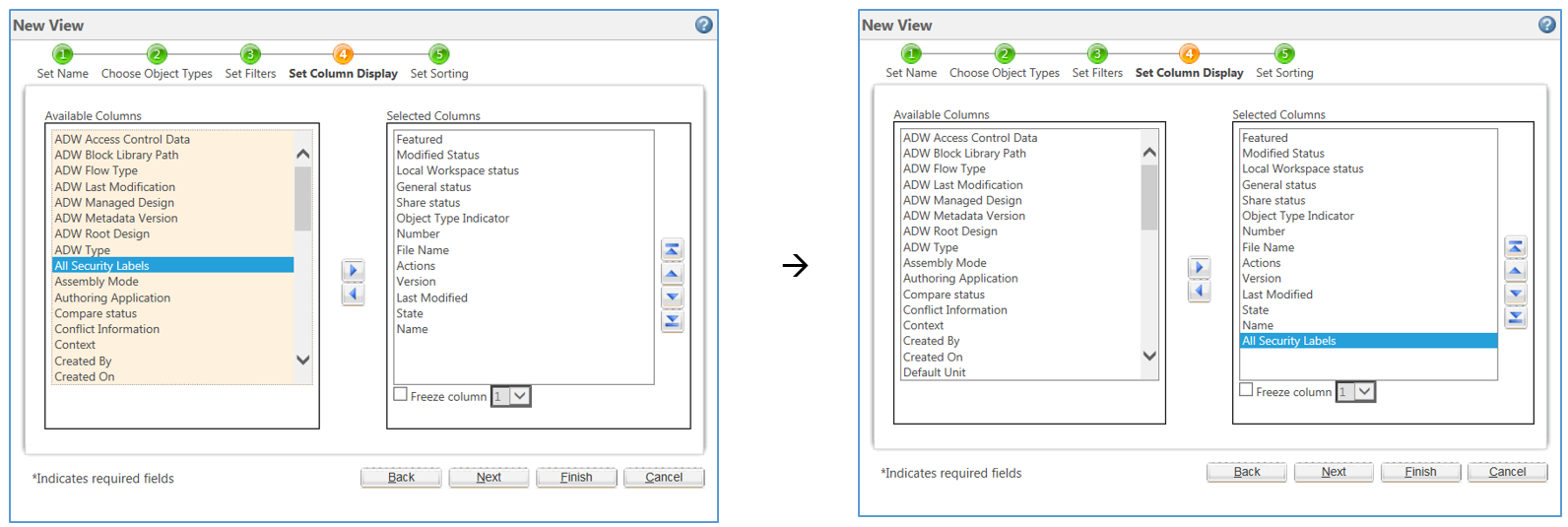
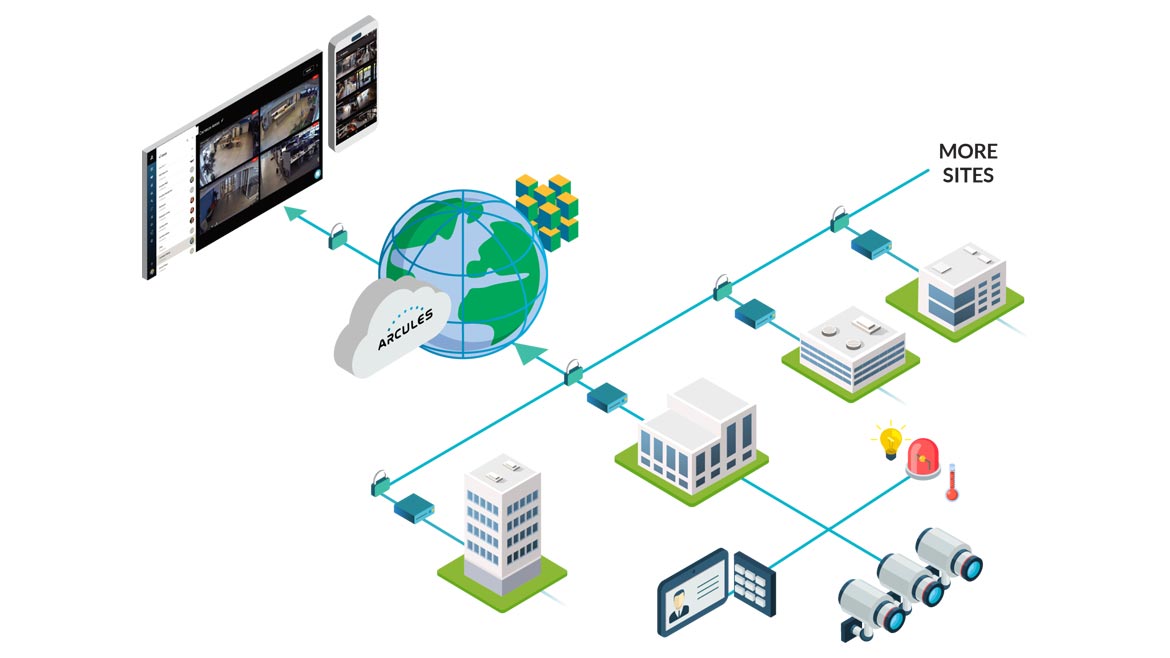
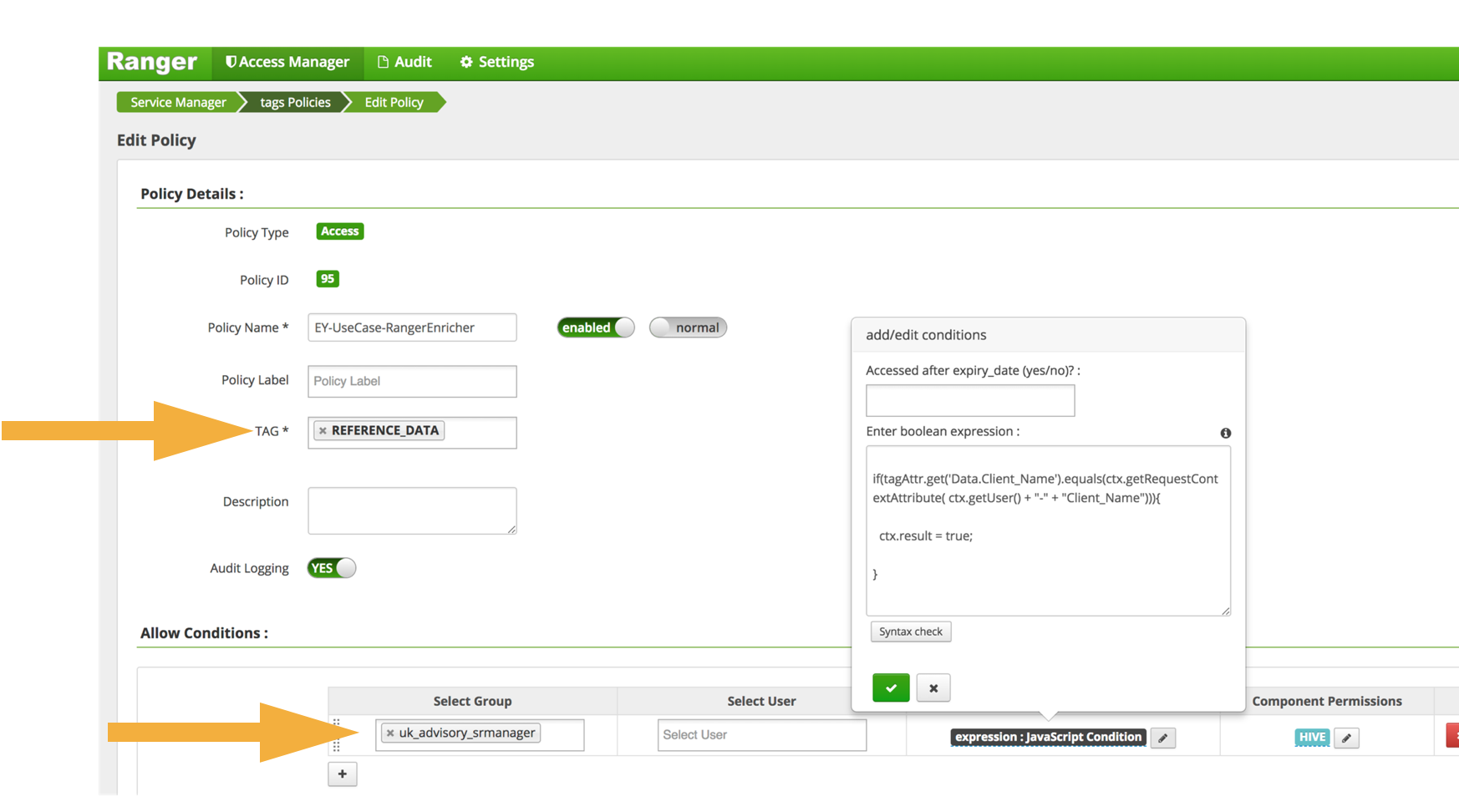
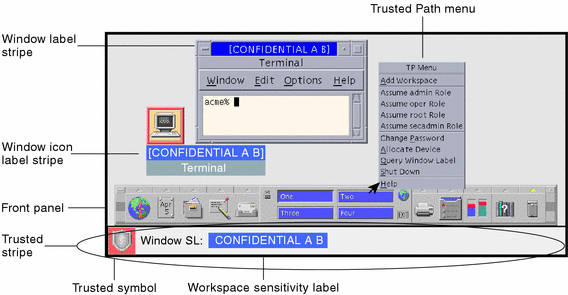
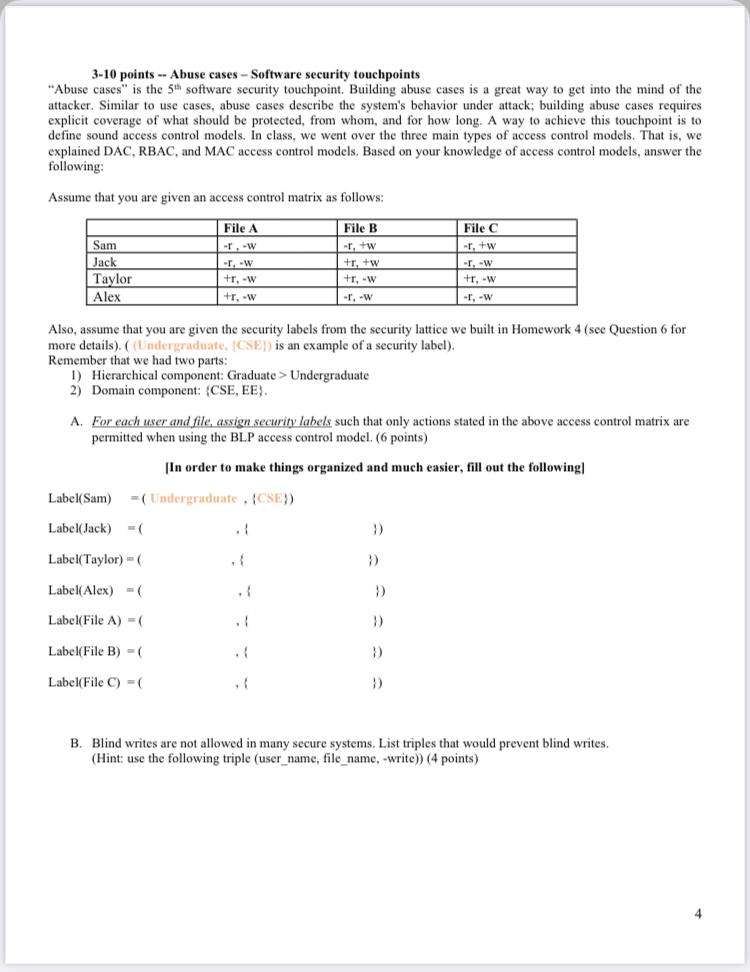
38 security labels access control
Web Content Accessibility Guidelines (WCAG) 2.0 - W3 Dec 11, 2008 · Abstract. Web Content Accessibility Guidelines (WCAG) 2.0 covers a wide range of recommendations for making Web content more accessible. Following these guidelines will make content accessible to a wider range of people with disabilities, including blindness and low vision, deafness and hearing loss, learning disabilities, cognitive limitations, limited movement, speech disabilities ... Security - ArchWiki - Arch Linux Labels-based access control means the extended attributes of a file are used to govern its security permissions. While this system is arguably more flexible in its security offerings than pathname-based MAC, it only works on filesystems that support these extended attributes.
Gerrit Code Review - Access Controls - Google Open Source This security feature tries to prevent a role with Run As capability from modifying the access controls in All-Projects, however modification may still be possible if the impersonated user has permission to push or submit changes on refs/meta/config. Run As also blocks using most capabilities including Create User, Run Garbage Collection, etc ...
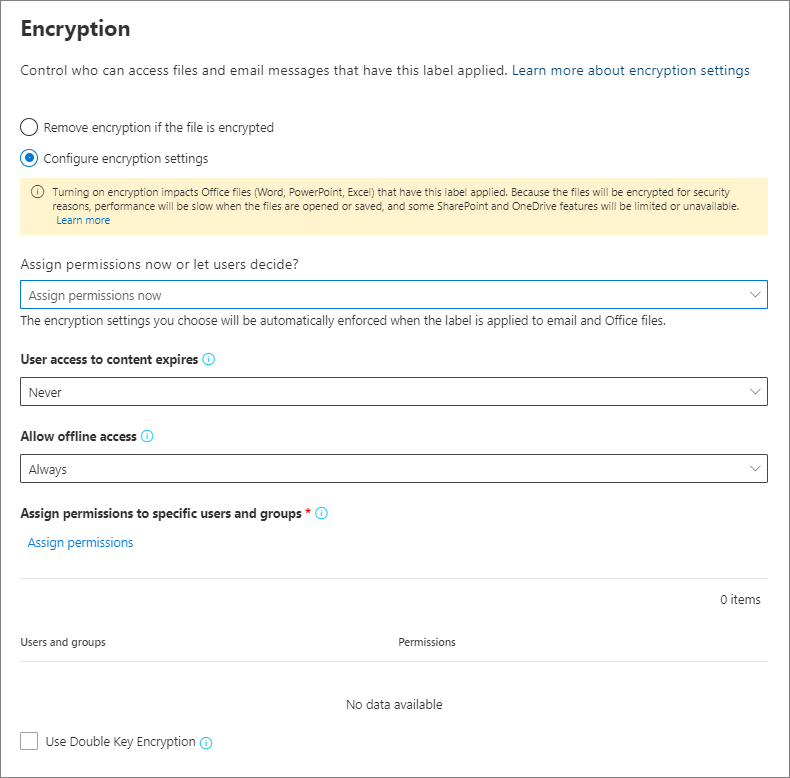
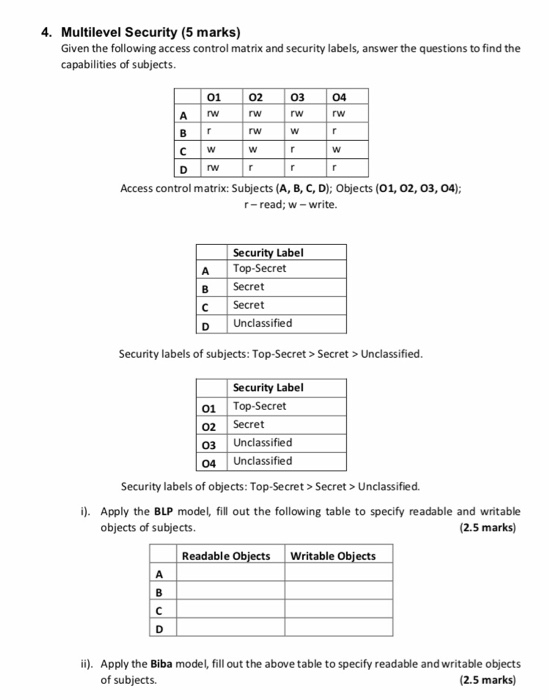
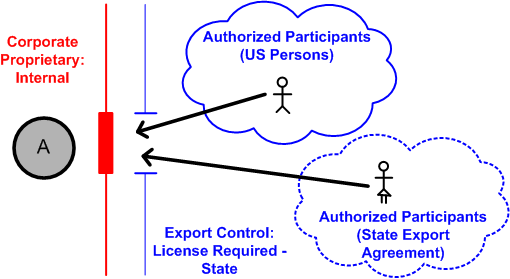
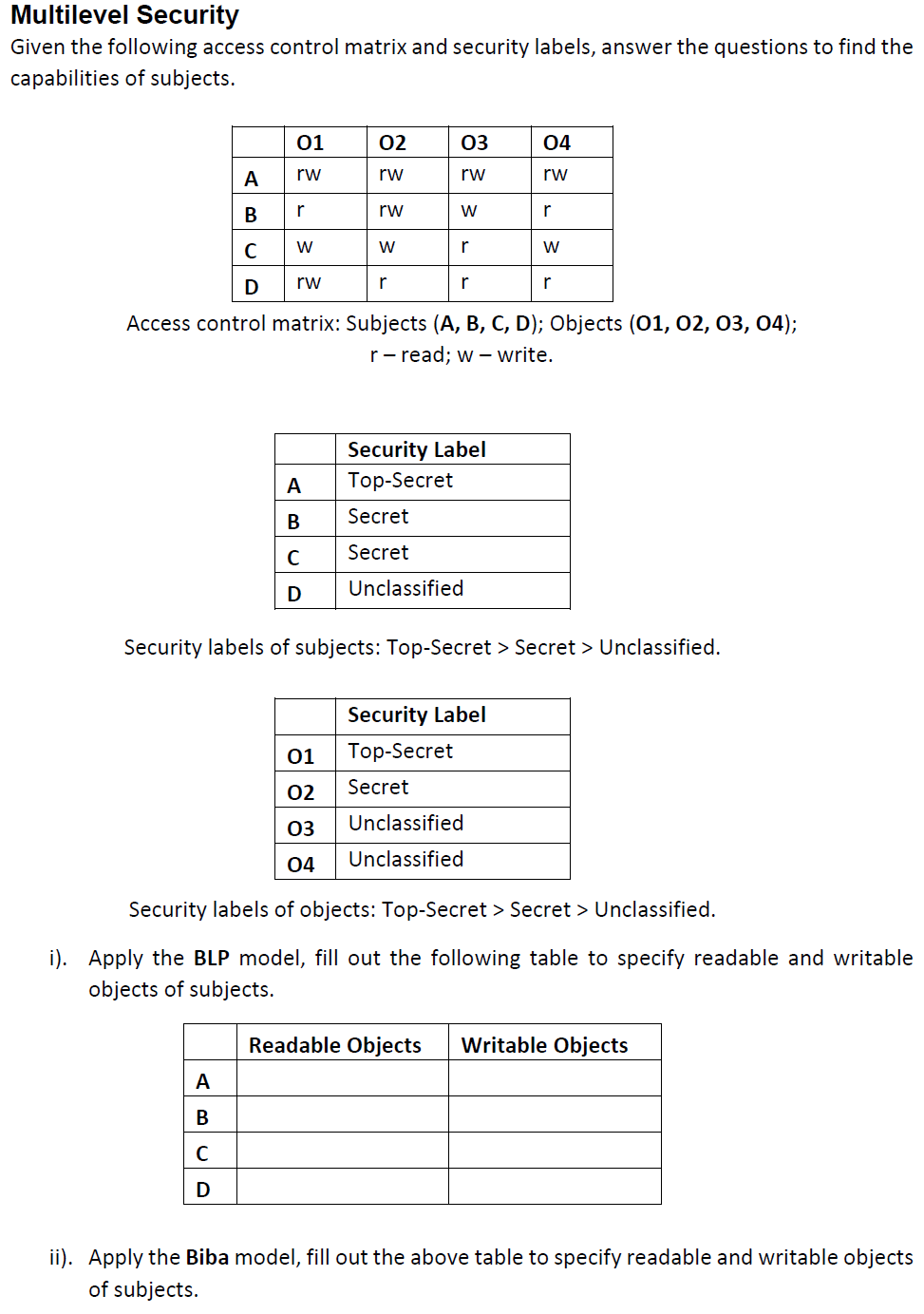
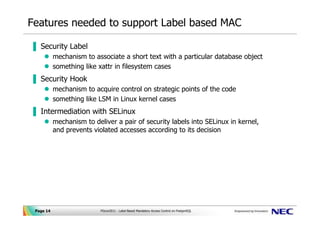
Security labels access control
Access Control Models: MAC, DAC, RBAC, & PAM Explained Management burden — A dedicated organizational structure must manage the creation and maintenance of security labels. What is discretionary access control (DAC)? Discretionary access control decentralizes security decisions to resource owners. The owner could be a document’s creator or a department’s system administrator. Configure a Security Context for a Pod or Container | Kubernetes Sep 30, 2022 · A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to: Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID). Security Enhanced Linux (SELinux): Objects are assigned security labels. Running as privileged or unprivileged. Linux ... Information security - Wikipedia The CIA triad of confidentiality, integrity, and availability is at the heart of information security. ( The members of the classic InfoSec triad—confidentiality, integrity, and availability—are interchangeably referred to in the literature as security attributes, properties, security goals, fundamental aspects, information criteria, critical information characteristics and basic building ...
Security labels access control. Products - Red Hat Customer Portal Infrastructure and Management Red Hat Enterprise Linux. Red Hat Enterprise Linux (RHEL) is the world's leading open source operating system that provides an intelligent, stable, and security-focused foundation for modern, agile business operations. Information security - Wikipedia The CIA triad of confidentiality, integrity, and availability is at the heart of information security. ( The members of the classic InfoSec triad—confidentiality, integrity, and availability—are interchangeably referred to in the literature as security attributes, properties, security goals, fundamental aspects, information criteria, critical information characteristics and basic building ... Configure a Security Context for a Pod or Container | Kubernetes Sep 30, 2022 · A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to: Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID). Security Enhanced Linux (SELinux): Objects are assigned security labels. Running as privileged or unprivileged. Linux ... Access Control Models: MAC, DAC, RBAC, & PAM Explained Management burden — A dedicated organizational structure must manage the creation and maintenance of security labels. What is discretionary access control (DAC)? Discretionary access control decentralizes security decisions to resource owners. The owner could be a document’s creator or a department’s system administrator.





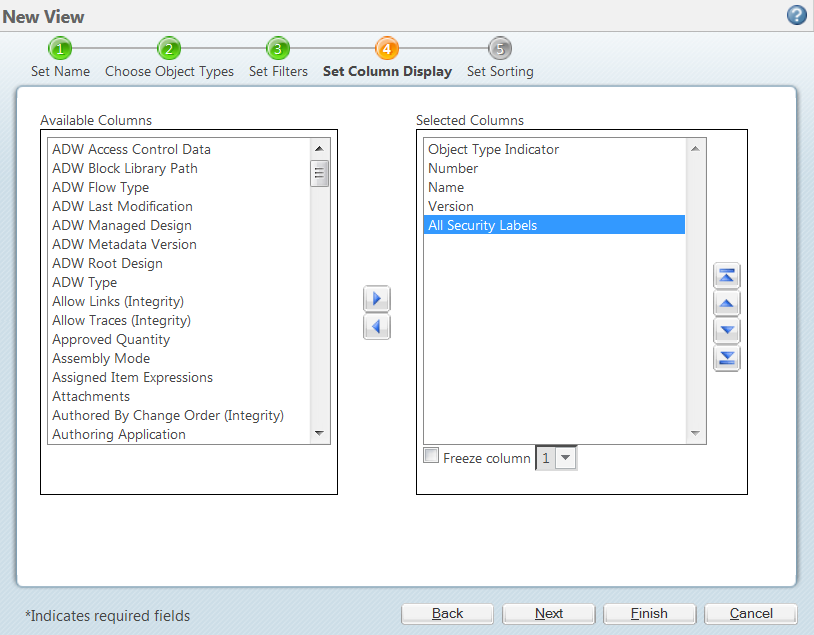




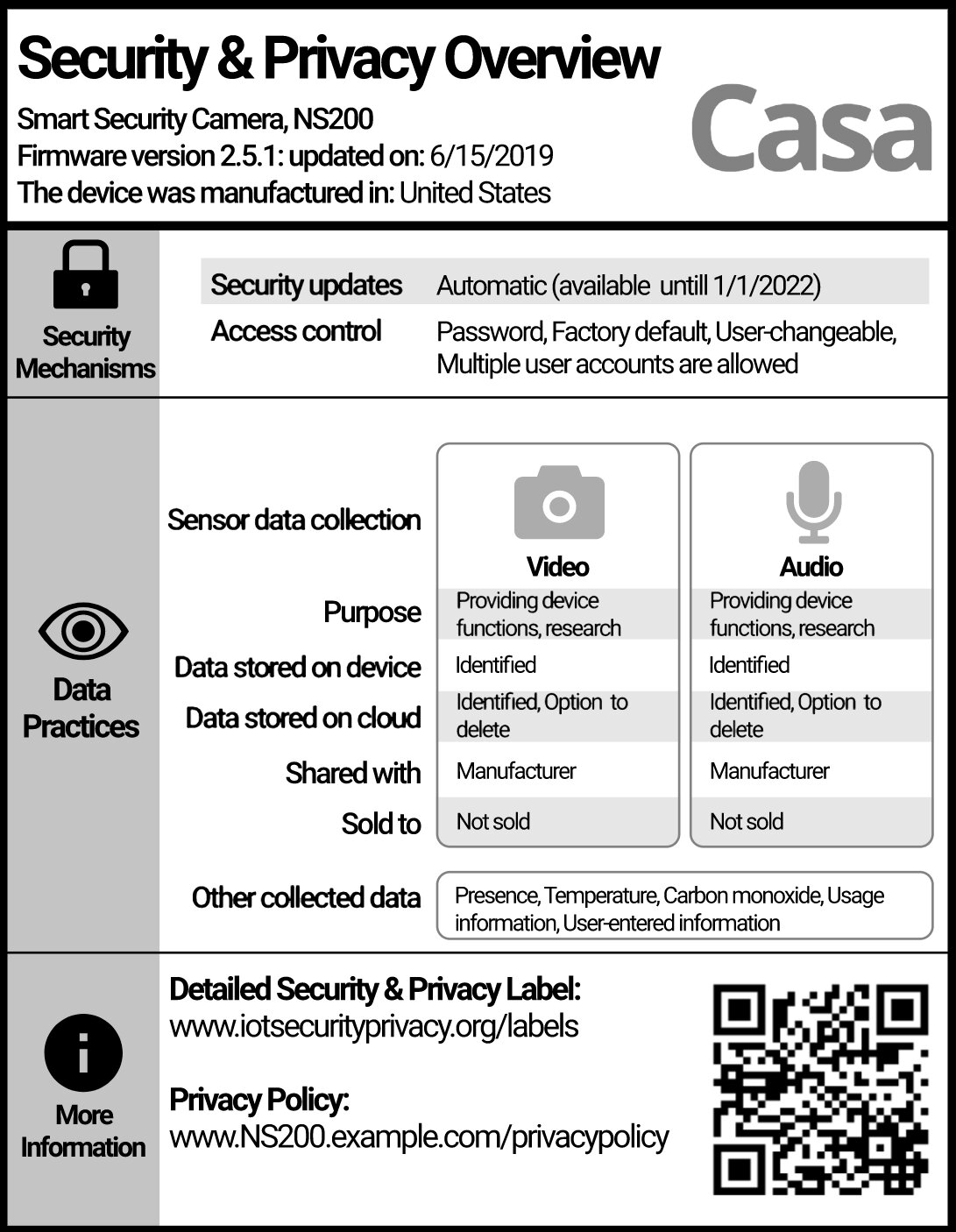

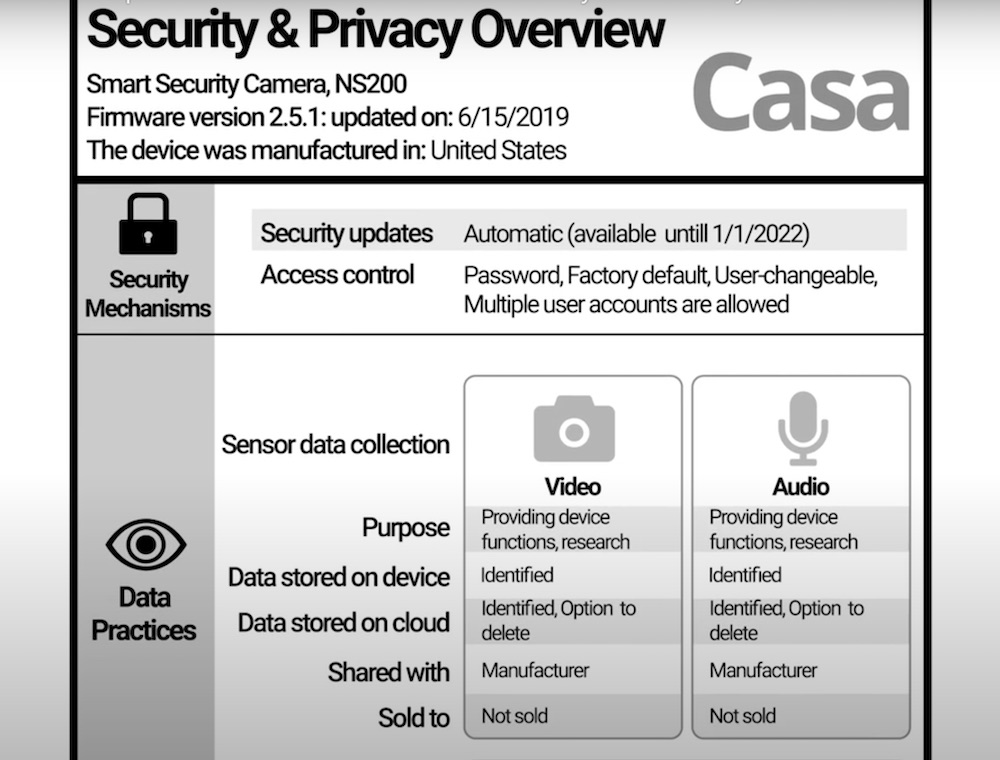












Post a Comment for "38 security labels access control"